A homoglyph is when a glyph (or character) from one character set looks identical to that of another character set. For example, the lower-case letter “а” from the Cyrillic alphabet appears to be identical to the lower-case letter “a” from the Latin alphabet.
While seemingly identical to the human eye, they are very different for a computer. Pasting a string that contains each of these characters into a web browser will take you to very different places.
Homoglyphs are frequently used in URL impersonation attacks because their substitution is indistinguishable to the human eye.
Homoglyphs are also more effective than other forms of impersonation, such as replacing lowercase “m” with “rn,” which can look almost identical in some fonts—for example, arnazon.com versus amazon.com. Or impersonation that preys on common misspellings—for instance, micosoft.com
So just how identical can a homoglyph attack be? In the next section, we will explore an example.
Note: To keep everyone safe, we have used screenshots for all impersonated domains.
Creating a homoglyph
To create an impersonated domain, we are going to use the Homoglyph Attack Generator at irongeek.com. From this page, we first need to type in the domain we want to impersonate. I am going to use supertekboy.com.
The generator then allows us to swap out each letter with a letter from another character set. The first two rows are the Latin character set in upper and lower case. However, several other character sets, including Cyrillic, are included.

Using the generator, we can switch one or more letters with those from a different character set. Let’s change the Latin letter “e” for the Cyrillic letter “e” (Unicode 435). This gives us the output below. Can you tell the difference?

If you were to click that link or cut and paste the URL into a browser, you would be redirected to the following URL.
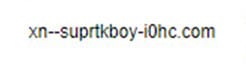
Were a bad actor to register this redirected domain, they could use it as a launchpad for any number of attacks, such as delivering a malicious payload, social engineering, or password capture. (I believe some domain registrars are blocking these types of domains).
Thankfully, if you cut and paste this impersonated URL into a modern browser, such as Microsoft Edge, it will identify the target URL before you click enter. But this could be easily overlooked by some users.
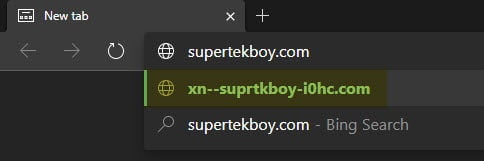
If this impersonated URL was received via email, it might be less obvious unless you hover over the URL to check its target.
Protection for URL Impersonation
The better solution is to use a product such as Microsoft Office 365 Advanced Threat Protection (ATP), specifically Safe Links, to protect your inbox.
Safe Links scans every URL transmitted via email. If the URL is deemed to be malicious, and the user clicks the link, Safe Links will warn the user of the malicious website. This is a great learning tool for users.
An administrator can configure Safe Links to allow a user to click through to the original URL (and accept the risk) or block the user from proceeding. The screenshot below is an example of a user prohibited from continuing to the original URL.

Safe Links has also been extended beyond the inbox and now protects links in all Office documents, such as Word and Excel, as well as in Microsoft Teams.
When configuring Safe Links I want to bring attention to two often overlooked options.
First is Apply Safe Links to email messages sent within the organization. If an internal user were to unknowingly send a malicious URL to another internal user this option would protect you.
Second is Do not let users click through safe links to the original URL. This option prevents the user from proceeding to a malicious URL despite being warned. A legitimate URL can always be whitelisted retroactively.
For more information on how to configure Safe Links and Office 365 ATP, be sure to check out Set up Office 365 ATP Safe Links policies.

I would love to know what URL impersonation attacks you have seen. Were they using homoglyphs? Drop a comment below or join the conversation on Twitter @SuperTekBoy.

Leave a Reply