This
As always, test these updates in a lab first! I recommend checking out this 7-part guide on configuring Exchange in your lab. It doesn’t take much to get one going.
The updates are as follows:

Exchange 2019 Cumulative Update 2 (VLSC)| KB4488401

Exchange 2016 Cumulative Update 13 | KB4488406 | UM Language Pack

Exchange 2013 Cumulative Update 23 | KB4489622 | UM Language Pack

Exchange 2010 SP3 Rollup 27 | KB4491413
The final countdown – 208 days left for Exchange 2010
Here is a quick reminder that extended support for Exchange 2010 is coming to an end. After January 14th, 2020, no further technical support or updates will be available. This includes security, bug and time zone updates.
Unfortunately, there is no direct path to Exchange 2019 from 2010. If you do plan to stay on-prem you will need to migrate to either 2013 or 2016 (I’d recommend 2016 as 2013 is now in extended support). From there you can migrate to 2019. Alternatively, you can migrate to Office 365.
For more information about the Exchange 2010 life-cycle check out the Exchange Team blog.
So, what’s new in these Cumulative Updates?
In the last set of cumulative updates, Microsoft reduced the number of permissions Exchange had in Active Directory. In an ongoing effort to further tighten the security posture of Exchange, Microsoft has further reduced Exchange’s permissions in Active Directory.
This includes two notable changes. The first is that Exchange can no longer assign service principal names (SPN). Second, a deny attribute has been added to the DNS Admins group. The Exchange Team determined neither of these rights was necessary for the operation of Exchange.
In the previous Exchange 2019 cumulative update, you could disable legacy protocols on a per-user basis. In cumulative update 2, you can now globally disable legacy authentication at the organization level.
This series of updates also introduces support for .NET Framework 4.8. While optional now, 4.8 will be mandatory as part of the December 2019 updates.
If you are current on your Exchange updates then these cumulative updates will not extend the schema. If you are running Exchange 2013 or Exchange 2016 prior to CU7, you will need to perform a schema update.
While these updates do not contain any changes to the schema, you will need to run SETUP /PrepareAD to apply these security changes. If you are running multiple versions of Exchange in coexistence, run SETUP /PrepareAD from the newest version of Exchange. For example, if you have Exchange 2013 and Exchange 2019, run SETUP /PrepareAD from Exchange 2019 CU2.
Note: If you are running in a multi-domain environment, you will need to perform SETUP /PrepareDomain in each domain. You do not need to run /PrepareDomain in the domain where you performed /PrepareAD. /PrepareAD also invokes the /PrepareDomain process.
Visual C++ 2013 Redistributable is a requirement for updating mailbox servers to Exchange 2013 CU23, Exchange 2016 CU13 & Exchange 2019 CU2. You will need to install this before running the setup. If this package is missing, setup will not continue. Edge Transport and the management tools require Visual C++ 2012 Redistributable.
For a full list of bug fixes be sure to check out the knowledge base links at the top of this article.
More Awesome News
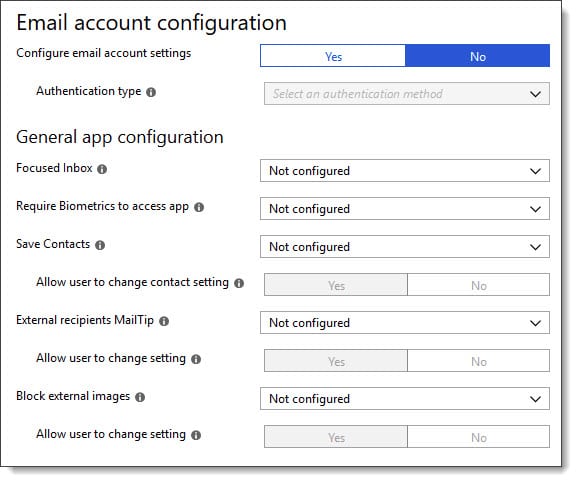
Outlook Mobile App Configuration Policies
In the article New Outlook for iOS and Android App Config Policy, Ross Smith announces some of the application settings that can be controlled via an application configuration policy.
These settings include whether to disable the Focused Inbox or, require biometrics to access the Outlook Mobile app. Some settings such as Save Contacts or MailTips provide additional options such as whether a user is allowed to override the administrator’s default configuration.
Older algorithms on the chopping block
Microsoft previously announced that older algorithms used in the transfer of mail in Exchange Online were being deprecated. This included SSL 3.0, TLS 1.0 and TLS 1.1. At the time of writing, Microsoft has since disabled SSL 3.0.
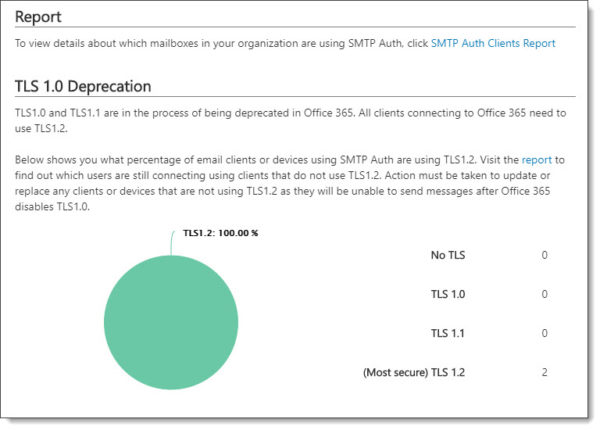
While Microsoft has no deadline to disable TLS 1.0 for mail transfer, they have announced that if an exploit is found they will quickly disable the protocol. Microsoft states that approximately 5% of all mail to Office 365 still uses TLS 1.0. Microsoft urges its customers to get to TLS 1.2.
To help identify which devices and applications are still using older TLS protocols you can access the SMTP Auth Clients report in the Mail Flow Dashboard in the Security and Compliance Center.
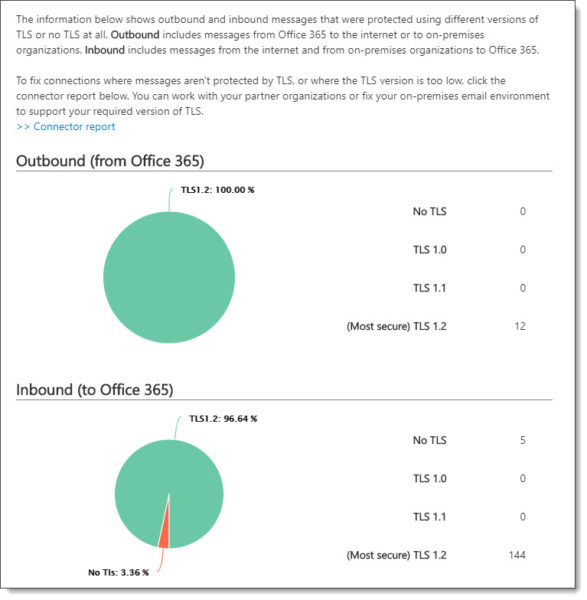
To identify all other SMTP connections to Office 365, including those made via hybrid mail flow to your on-prem Exchange servers, check out the Messages Protected in Transit (by TLS) report. This is also located in the Mail Flow Dashboard in the Security and Compliance Center.
Exchange 2019 will require hybrid for modern auth
During an Ignite 2017 session with Greg Taylor, it was announced that modern authentication was coming to Exchange 2016 and, was planned for Exchange 2019 which had not yet been released.
Modern authentication provides a number of benefits. Most notably that it allows you to tie in technologies such as multi-factor authentication with Exchange on-prem. In turn, any modern Outlook client could then be authenticated through multi-factor, or, any other mechanism delivered by your identity provider; whether that be Active Directory Federation Services, or, a third party like PingID or Duo.
For Exchange 2016 this would require a hybrid connection with Office 365 and be termed Hybrid Modern Authentication or HMA. For Exchange 2019 modern authentication would be natively built into the codebase and not require a hybrid connection.
The Exchange Team delivered on HMA for Exchange 2016. However, it was announced in a recent blog post that modern authentication without a hybrid connection is no longer being pursued. This means that Exchange 2019 will require a hybrid connection to Office 365 to support modern authentication.
Exchange 2019 Calculator
The Exchange 2019 Server Roles Requirements Calculator has been released. It is worth noting that this calculator is unique to Exchange 2019 deployments only. If you are deploying older versions of Exchange, such as 2013 or 2016, you will need to use the old calculator.
The new calculator takes into account a number of technologies unique to Exchange 2019, such as the MetaCache Database, and improves on the old calculator, for example, better virtualization calculations.
The Exchange 2019 calculator is bundled with the Exchange 2019 ISO, which is available at the Volume License Service Center (VLSC), or, the Microsoft Developer Network (MSDN).
Modern Auth for Managed Tenants
Back in April Microsoft announced that any managed tenant created before August 1st, 2017 would be fully switched to modern authentication.
Currently, only specific clients, such as Outlook for Mac, Outlook on the Web and Outlook Mobile are enabled for modern authentication. Microsoft is now extending this to all remaining clients in a managed tenant, including Outlook for Windows and Skype for Business.
Note: A managed tenant is any tenant using Password Hash Sync, Passthrough Authentication, or, Cloud Only identities. Federated tenants, that leverage Active Directory Federation Services (or a third party identity provider) will not be switched.
Essentially what this looks like to end users is a different login prompt. Rather than the traditional basic authentication prompt we have seen in Windows for years, they will now see the following modern authentication prompt.

Hybrid Agent Update
The Hybrid Agent allows an organization to perform mailbox moves and free/busy lookups with Office 365 without publishing your on-premises Exchange to the internet.
In April, Microsoft released an update to the Hybrid Agent. This update addresses a number of high availability scenarios, including being able to deploy multiple agents in your environment and being able to register the URL of a load balancer rather than being restricted to a single Exchange server.
Keep in mind that this release of the Hybrid Agent does not address things like hybrid mail flow (which will still require inbound port 25), mail tips, message trace, and mailbox search. It is possible these features will come in later versions of the Hybrid Agent. At present, the hybrid agent does not work with GCC High or DoD tenants.
For more information on the Hybrid Agent be sure to check out Jeff Kizner’s Ignite session. You can find notes and timers on this session in the article 15 Ignite sessions every Exchange admin should see (it’s the second session on the list).
Exchange Online cmdlets & Azure Cloud Shell
The Exchange Team has announced the availability of the Exchange Online PowerShell Module in Azure Cloud Shell. Azure Cloud Shell is a web-based version of PowerShell that can be launched from within any web browser by navigating to shell.azure.com, or, clicking the PowerShell icon in the Azure portal.
Once connected you can issue the Connect-EXOPSSession cmdlet to import all Exchange commands. Azure Cloud Shell offers upload and download options to import and export scripts and other data. Azure Cloud Shell does require that Azure Cloud Storage be allocated to each Cloud Shell user.

Public Folders
Microsoft announced the Public Folder Consistency Agent for Exchange Online. This agent performs two tasks.
The first is the agent will look for orphaned permissions on public folders and remove them. Orphaned permissions can occur when a user is assigned rights to a public folder and then that user is subsequently deleted. Despite the user being removed, the permission remains.
The second is the agent will resolve an attribute mismatch, which could cause mail addressed to a mail-enabled public folder to become queued. Once the agent corrects the attribute, mail will flow to the public folder once more.
Both of these features are part of a new automated agent, so no administrator intervention is required.
Unified Messaging
In February 2020, Unified Messaging in Exchange Online will be retired. This follows the announcement of Unified Messaging being dropped from Exchange 2019 back in October. It also marks the end of Unified Messaging in the Exchange product line.
Customers leveraging Exchange Online Unified Messaging for either Skype for Business 2015 or Lync 2013 will be automatically transitioned to Cloud Voicemail. Microsoft announced this transition will be transparent to end users, begin in March 2019, and customers will receive transition notifications as early as February. Organizations on Lync 2010 will not be transitioned. Anyone on Lync 2010 will need to migrate to Skype for Business to use Cloud Voicemail.
Customers leveraging Exchange Online Auto-Attendant will need to manually transition attendants and phone numbers to Cloud Auto-Attendant before February 2020.
The main benefit of this change is that it folds all products–Skype for Business on-premises, Skype for Business online, and Teams–into the same voicemail and phone system. This allows Microsoft to focus all development and support onto a single product.
More In Awesome
Microsoft has been developing a migration a solution that will migrate mail, contacts, and calendar items from Google G-Suite to Office 365 using IMAP. You can read more about it, and its limitations, here.
Need a refresher from Ignite 2018?
With Ignite 2019 only a few months away it might be time to brush up on some of the topics covered at the last Ignite. If you need a refresher on all the email messaging features announced at Ignite, I highly recommend checking out the article 15 Ignite sessions every Exchange admin should see (2018 edition). In this article, there are extensive notes on what each session contained. In addition, those notes contain timers if you need to jump to a specific topic.

So what do you think is coming next? What would you like to see? Drop a comment below or join the conversation on Twitter @SuperTekBoy.

Leave a Reply