Ever wonder, Who made that modification to my Exchange environment?
I have.
So how do we answer that question?
Behold! The great and powerful Admin Audit Log!
The Admin Audit Log was introduced in Exchange 2010. But, it still seems a best-kept secret. There are a couple of ways to get to it.
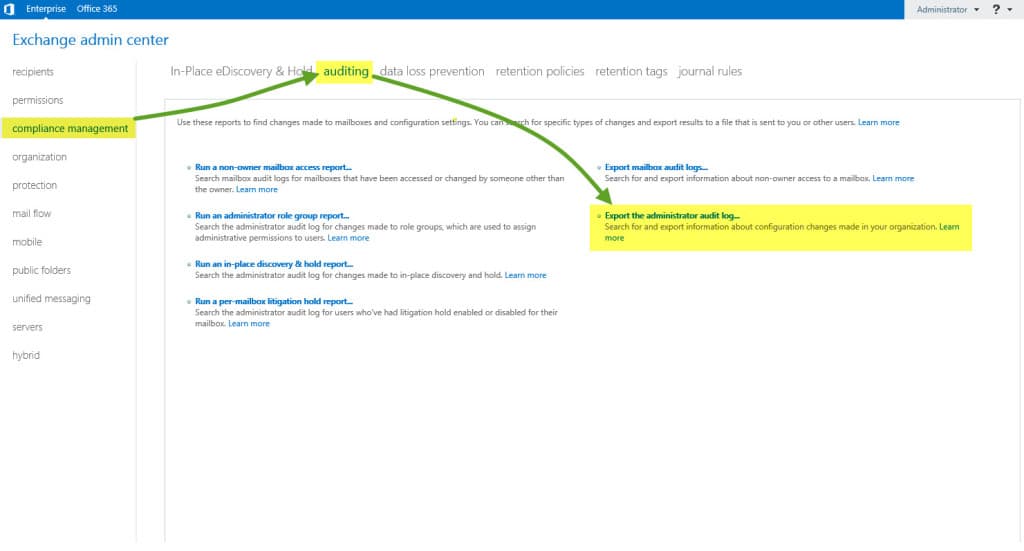
First, you can go through the EAC >> Compliance >> Auditing tabs. Then select Export Administrator Audit Log.
The second is via the Exchange Management Shell (EMS) through the Search-AdminAuditLog cmdlet. Let’s explore this method a little more.
Search-AdminAuditLog
If you just type Search-AdminAuditLog with no parameters it will return the last 1,000 items. You can increase this response with the -ResultSize parameter. Depending on the size of the environment this could return a lot of results. You may quickly find your results have been truncated by the screen buffer.
Note: The default screen buffer for EMS is 300 lines. You can increase this by right-clicking on the EMS icon and selecting Properties from the context menu. Select the Layout tab. Then change the Height under Screen buffer size.
If you need the entire log, a better alternative may be to dump it to a file.
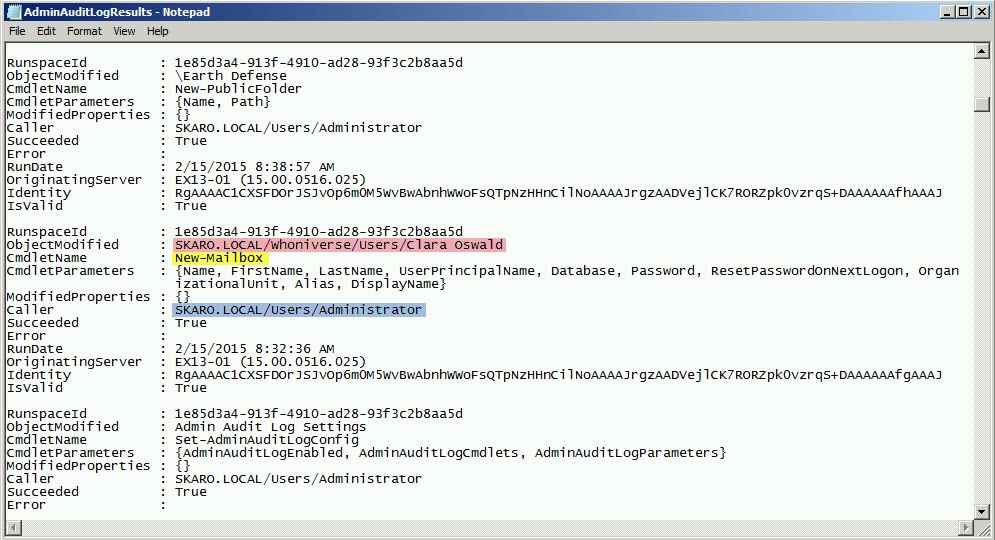
C:\> Search-AdminAuditLog >> C:\AdminAuditLogResults.txt
The end result will look like this. As you can see in the screenshot, the Administrator ran the New-Mailbox cmdlet to create a mailbox for Clara Oswald.
Another option could be to export the data to a CSV file.
C:\> Search-AdminAuditLog | Select-Object rundate,caller,cmdletname,objectmodified | Export-CSV C:\AdminAuditLogResults.csv
Our command generates a file with four columns. These are the items we identified with Select-Object.
Building a dam
But what if we don’t need the entire log? To avoid the flood lets apply some parameters.
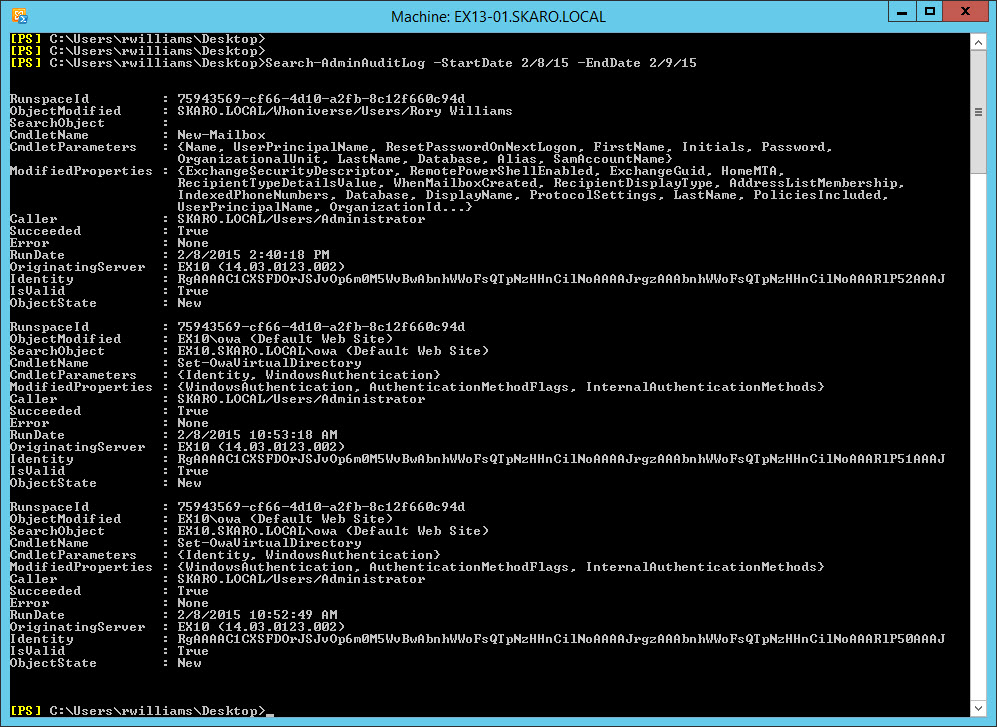
We can filter the log to just show events between two dates. For this, we can use the -StartDate and -EndDate switches.
In the above screenshot (click to enlarge) three different events occurred on February 8th.
The first was the creation of a new mailbox by the Administrator for Rory Williams.
The next two events were modifications to the OWA virtual directory on a server called EX10. From the hostname (and also the build number) we know this is an Exchange 2010 server.
We can see the Administrator used the Set-OWAVirtualDirectory cmdlet and specified the WindowsAuthentication parameter. We see both commands ran successfully.
We don’t have to specify both the start and end dates. We can use just one. Depending on which will extend the range to either the oldest log entry or the newest log entry.
But, what if we just want to see all actions performed on a specific object?
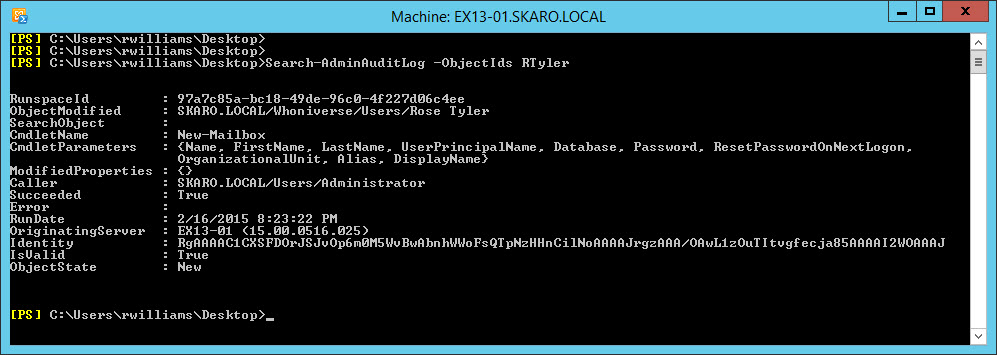
Easy. We specify -ObjectIds. Let’s see all actions taken against user Rose Tyler. Her alias is rtyler.
Only one entry has been recorded for Rose. We see the Administrator created a mailbox for her on February 16th at 8:23 pm.
Another option is to filter by Exchange administrator.
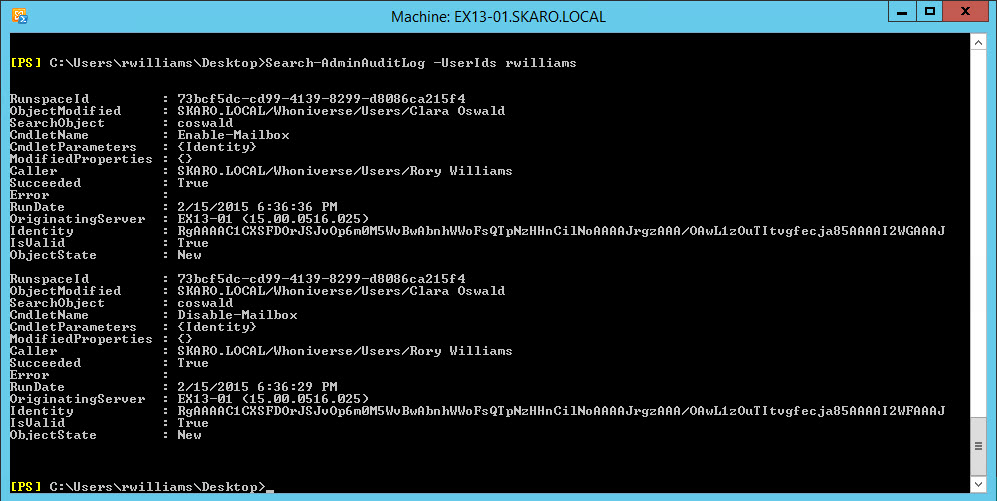
For this, we can use the -UserIds parameter. Let’s see what junior admin Rory Williams has been up to.
From the response, we can see Rory performed two actions. Both of these actions involved Clara Oswald. The first was to disable her mailbox. The second was to enable her mailbox. This is a great way to track what each team member has done.
Perhaps we are just interested in looking for all instances of a certain command.
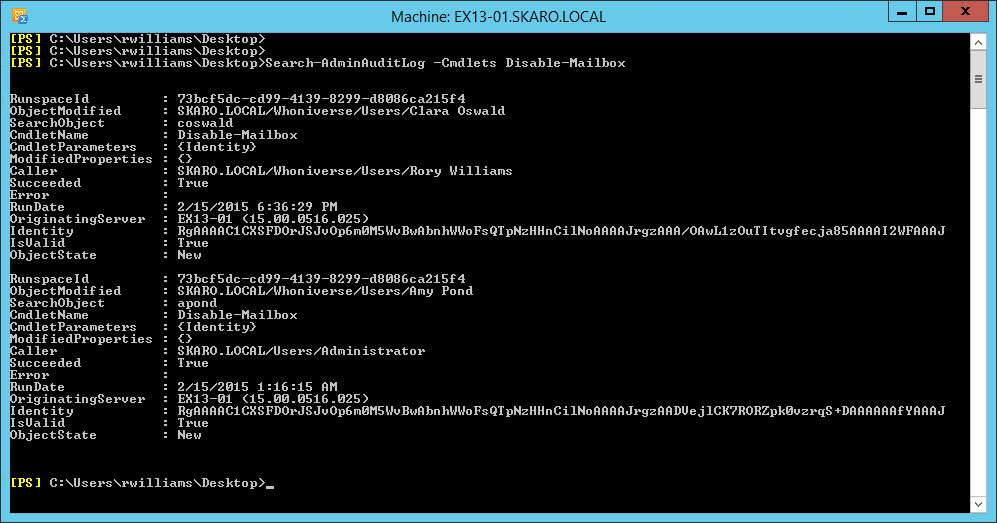
For this we specify the -Cmdlets switch. We can also narrow -Cmdlets down with -Parameters switch. Let’s find out how many times Disable-Mailbox has been used.
From the output, we can see Disable-Mailbox has been used twice. The first time the Administrator disabled Amy Pond. The second time Rory Williams disabled Clara Oswald.
We can also combine all these parameters. For example, if we wanted to look for all instances of the Disable-Mailbox cmdlet within a date range and performed by Rory Williams, our command would resemble this.
C:\> Search-AdminAuditLog -Cmdlets Disable-Mailbox -StartDate 02/15/15 -EndDate 02/16/15 -UserIds RWilliams
What is logged
Out of the box, Exchange keeps a track of all admin actions performed over the last 90 days. You can check these settings using the Get-AdminAuditLogConfig cmdlet.
If we want to change the number of days we can use the following cmdlet.
C:\> Set-AdminAuditLogConfig -AdminAuditLogAgeLimit 365.00:00:00
In this example, we set the log for 1 year. We specify this in the DD.HH:MM:SS format. Beware setting the value to all zeroes. This will empty the entire log.
Another option is how much information we want to see. With LogLevel set to Verbose, we get more detail. Such as a before and after picture of the affected object. This might prove useful if you are unsure what the old setting was and need to revert.
By default, the log records all cmdlets with the exception of Get- variants. If we wanted to exclude additional cmdlets we could use the following.
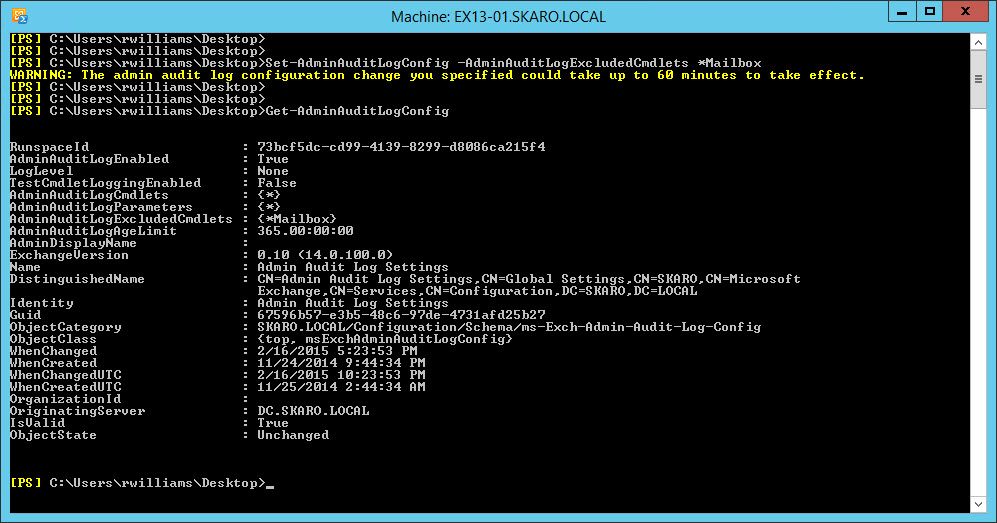
C:\> Set-AdminAuditLogConfig -AdminAuditLogExcludedCmdlets *Mailbox
In this example, we have excluded all Mailbox cmdlets with a wildcard. We receive a warning that this change could take up to 60 minutes. Its latency depends on AD replication and in my lab the change is instantaneous.
When I run Get-AdminAuditLogConfig the change is already apparent.
To revert, repeat the command but use $Null instead.
To include, rather than exclude, you can utilize the command below. Similar to exclude you can use wildcards. You can also use commas to specify multiple commands. For example, if you were only interested in auditing changes to a couple of commands, it may resemble this.
C:\> Set-AdminAuditLogConfig -AdminAuditLogCmdlets *Mailbox,*MailboxDatabase
In this example, we will only monitor a command that ends in Mailbox, or, MailboxDatabase. So, Set-Mailbox, New-Mailbox, Disable-Mailbox to name a few. Exchange will not log any other commands run in the environment.
To revert you must use a wildcard. If you were to use $null logging would essentially be disabled.
C:\> Set-AdminAuditLogConfig -AdminAuditLogCmdlets *
So, what do you think? Powerful right?
I’d love to hear your experiences using the Admin Audit Log. Drop a comment below.



amzing