Block Outlook for Android on wearables and smartwatches
Microsoft has added a policy to Intune that grants an administrator the ability to block Outlook for Android on wearable devices (for example, a Samsung Galaxy Watch). This block prevents any Outlook data from being shared with the wearable device. This includes emails, calendar items, and more.
To configure this block, log into Endpoint Manager and select the Apps > App Configuration Policy tabs. From here, click Add and choose Managed Apps (you can also modify an existing Outlook app policy).
Give the policy a name and click Select public apps. Search for, and add Microsoft Outlook. Click Next.

On the Settings tab, expand Outlook configuration settings, and next to the field Org Data on Wearables select No. From here select any other settings to go into your App Configuration Policy and click Next. On the next screen pick which users or groups of users will get this settings. Click Next and Create.

For those who do not have an Intune subscription, a new feature is being added to mobile device policies in Exchange Online (which anyone with an Exchange license can leverage) to disable Bluetooth on the device. You can do this via PowerShell. In the example below, we are disabling Bluetooth for the policy named, Company Mobile Policy.
C:\> Set-MobileDeviceMailboxPolicy -Identity "Company Mobile Policy" -AllowBluetooth Disable
Global recipient limits
Earlier in the year, Microsoft announced a change to recipient limits in Office 365. Recipient limits dictate how many recipients someone can add to a single email message (this includes all recipients added to the To, Cc, and Bcc lines). This limit was previously hardcoded to 500 recipients. With the February announcement, administrators were allowed to configure this limit per mailbox, with a value of 1 to 1,000 recipients per message.
Starting in August Microsoft extended this functionality by allowing a global recipient limit to be set via PowerShell using the Set-TransportConfig command.
To see the current configuration, connect to Exchange Online PowerShell and run the following command.
C:\> Get-TransportConfig | Format-List MaxRecipientEnvelopeLimit MaxRecipientEnvelopeLimit : Unlimited
A value of Unlimited denotes the Office 365 published limits, which at the time of writing is 1,000 recipients per message.
You can modify this value with the following command. In the example below we are setting the max recipients per message to 500.
C:\> Set-TransportConfig -MaxRecipientEnvelopeLimit 500
In most cases, when this setting is configured on both the mailbox and globally, the mailbox will win. The exception to this is when the mailbox is set to Unlimited, then the global parameter wins. Another way to think of Unlimited at the mailbox and global level is null or not set.
Disable Legacy Authentication by Client
Microsoft has allowed administrators to easily disable legacy authentication by the client type. These settings are found in the main Microsoft 365 Admin Center, by navigating to Settings > Org Settings > Modern Authentication.
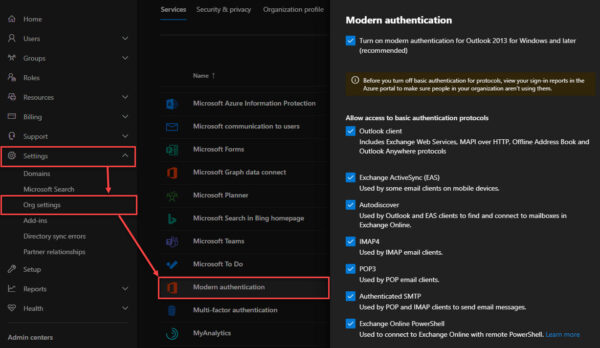
Deselecting each checkbox (and clicking save) will disable legacy authentication for that client protocol.
For example, unchecking Outlook client will prevent any Outlook client that does not support modern authentication from connecting. This means Outlook 2010, and unpatched Outlook 2013 clients, will no longer be able to connect.
Another example, unchecking Exchange ActiveSync (EAS), will prevent any native mail apps that do not support modern authentication from connecting. Alternatively, if all your mobile devices using Outlook for iOS or Android, you can also safely disable this checkbox.
Before disabling any legacy authentication, check the Sign-Ins report in Azure AD.
Note that these policies conflict with security defaults. If you have security defaults set to Yes, you won’t be able to use these policies. Security defaults mandate the use of modern authentication through a separate mechanism. If security defaults are enabled, the modern authentication tab will display the following message.

It is also possible to block legacy authentication through the use of Conditional Access Policies. Be sure to check your Conditional Access Policies before using the checkboxes under Org Settings > Modern Authentication tabs.
Legacy Authentication deadline extended till 2021
Microsoft previously announced that it was blocking legacy authentication in Exchange Online on October 13th, 2020. Due to the global pandemic, this date was postponed to the second half of 2021. Microsoft will propose an exact deadline in the coming months. After this date, any application connecting to Exchange Online will be required to leverage modern authentication (OAuth 2.0). Microsoft will continue to disable legacy authentication on any newly created Office 365 tenants.
For devices and applications that integrate with Exchange Web Services, such as voicemail, ticketing systems, or line of business applications, these will also be required to support modern authentication.
For PowerShell, I recommend using the Microsoft Exchange Online PowerShell Module. This module supports both modern-authentication and is a requirement if your admin account has multi-factor authentication enabled (which I hope it does!). I recommend checking out this article for more information on how to use this module. Also, you may want to look into the Azure Cloud Shell. Check out the tutorial; Using Exchange Cmdlets in Azure Cloud Shell.
For POP and IMAP, Microsoft recently added OAuth support. However, this still requires your POP or IMAP application to support OAuth. Microsoft will also be releasing a tool to help you identify active POP and IMAP users in Office 365 and what authentication mechanism they are currently using.
The most significant impact of this announcement will be to ActiveSync. ActiveSync is used by countless native mail apps to access their Office 365 mail. I highly recommend migrating your user base to Outlook mobile (for iOS and Android). Outlook Mobile supports both modern authentication and multi-factor authentication. It is worth noting that some native mail apps, such as those included in iOS 11, have added support for modern authentication. However, pushing users to Outlook Mobile, versus upgrading their phones, is the path of least resistance. Not to mention your helpdesk or IT department will only need to support one universal mail client.
To track which devices and applications are signing in with basic authentication, you can use the Azure AD Sign-ins dashboard. Microsoft covers this process in this article.
If you are interested in how to block basic authentication on-prem with Exchange 2019, check out this article, Disabling Legacy Authentication in Exchange Server 2019.
More in Awesome
Microsoft has deprecated the Intune connector for Exchange on-premises. Existing connectors will be unaffected, however, the ability to create a new connector has been removed. For customers wanting to leverage Intune with Exchange on-premises, they must configure Hybrid Modern Authentication instead.
Exchange Online PowerShell module v2 has now added support for using modern authentication with unattended scripts. Starting with module version 2.03 you can now use app-certificates to authenticate your script’s connection to Exchange Online.
Microsoft is changing how conditional access policies and Exchange Online device access rules coexist. At the time of writing, Outlook for iOS and Android ignore device access rules if a single conditional access policy is present (even if that policy does not define Outlook for iOS and Android as a condition). In the future, device access rules will only be ignored if conditional access policies are defined for Outlook for iOS and Android. You can read more about this change here.
Outlook for Android has added support for the new password complexity enhancements in Android 10. This was available at the end of August.
Further Reading
Here are some articles I thought you might like.
- Recover deleted email in a user’s mailbox
- Hybrid Configuration Wizard fails: WinRM client cannot process the request
- Use Log Parser Studio in your Exchange & Office 365 migration planning
- Blocking OneDrive may save attachments to the default SharePoint document library
- RPC/HTTP & Block Legacy Auth may prevent Outlook reconfiguration after migrating to Exchange Online

So what do you think is coming next? What would you like to see? Drop a comment below or join the conversation on Twitter @SuperTekBoy.

Great stuff! Thanks