Recover deleted mail using the new Exchange Admin Center in Office 365
In the last quarterly update, we covered the new Exchange Admin Center in Office 365. Exclusive to the new admin center is the ability to recover deleted items back into a user’s mailbox. This process has been available using PowerShell for some time.
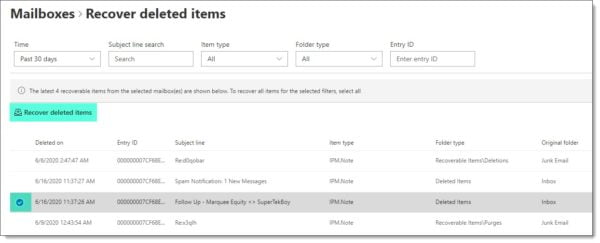
Keep in mind you can only recover up to the limit of your single item recovery policy. By default, this is 14 days in Office 365, but can be increased to 30 days (although you will need to set this ahead of time).
You can read more about how to recover deleted items in the following article.
Preventing Reply-All Storms in Exchange Online
Microsoft has added a new feature to combat reply-all storms. These storms are particularly prevalent when numerous people execute a reply-all to a massive distribution list.
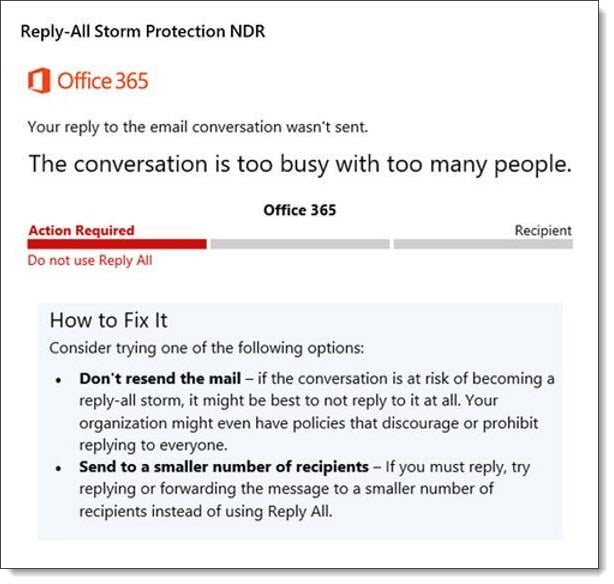
Microsoft’s initial reply-all protection will block replies to an email thread for 4 hours if it detects more than ten reply-all messages within 60 minutes to a thread with over 5,000 recipients.
The eleventh sender will receive a non-delivery report titled Reply-All Storm Protection with the reason the message was blocked.
Exchange Online to support DANE and DNSEC
Microsoft will be adding outbound support in the second half of 2020 for DANE and DNSSEC in Exchange Online. Inbound support will come in 2021.
DNSSEC digitally secures DNS records with certificates. This ensures that the DNS records have not been tampered with during transmission by a man-in-the-middle attack. This validates the authenticity of DNS records received by Exchange Online.
DANE (DNS Authentication of Named Entities) for SMTP is designed to prevent downgrade and man-in-the-middle attacks. These attacks can occur because STARTTLS always initiates communication with a remote server unencrypted to see if the receiving server supports TLS transmission. Even if TLS is established, its this early negotiation that could be vulnerable to a man-in-the-middle attack (which could also redirect mail transmission elsewhere).
DANE uses specialized DNS records (secured with DNSSEC) to allow servers to know the TLS capabilities of a remote party before transmission. This eliminates the need for the initial unencrypted handshake.
There is a really nice article on DANE published by APNIC.
Make sure you are running the latest Hybrid Configuration Wizard
In a post back in March, Microsoft announced version 17 of its hybrid configuration wizard. The wizard contains several significant changes, including smaller bug fixes and enhancements.
The first is that the wizard will no longer create or require a federation trust in some Exchange environments. If the wizard detects the presence of Exchange 2010, the federation trust will be created. However, if the on-premises environment only includes Exchange 2013 or newer, the federation trust is skipped. This means that domain proof is not required, which skips the need to create DNS TXT records as part of the wizard.
Second, the wizard also vastly improves how it reports OAuth errors if enablement fails during the execution of the wizard. Detailed OAuth failure messages are now reported in the HCW logs, which will help significantly with troubleshooting.
To get the latest version of the wizard, you need to log onto the Exchange Online Admin Center, select the Hybrid tab, and click the Configure button.
Despite the historically self-updating nature of the hybrid configuration wizard, users on older versions will need to uninstall and then reinstall version 17 from the portal. However, once installed, version 17 will check for updates on launch.
SMTP Auth to be disabled in new (and some existing) tenants
Microsoft announced that it would be disabling SMTP Authentication in new tenants by default. Microsoft further stated that it would disable SMTP Authentication in existing tenants who are not leveraging the technology.
SMTP Authentication is a technology that allows a device or application to relay mail via Exchange Online by providing a username and password. While Microsoft added support for OAuth 2.0 in SMTP Auth, many devices and apps simply do not support it.
For organizations that require SMTP Authentication, Microsoft has released granular controls to give administrators the ability to disable SMTP Authentication at a per mailbox level. This allows administrators to limit SMTP Authentication to mailboxes that require it. Administrators can also turn on SMTP Auth globally if they desire.
I have never been a big fan of relaying directly to Exchange Online and, by extension, SMTP Auth. While many environments openly allow outbound connections, I am a big fan of blocking outbound SMTP ports to only approved systems, such as your on-premises Exchange Servers. This prevents compromised devices from sending out spam or malware, which will eventually put your IPs on a blacklist.
I always recommend keeping all devices and apps relaying through an on-premises Exchange server. This allows you to restrict your outbound SMTP connections to just a pair of centralized servers, rather than turning your outbound firewall rules into swiss cheese.
Using Exchange Servers to relay also completely negates any concern around the changes to SMTP Authentication.
Basic Authentication deadline extended till 2021
Microsoft previously announced that it was blocking basic authentication in Exchange Online on October 13th, 2020. Due to the global pandemic, this date was postponed to the second half of 2021. Microsoft will propose an exact deadline in the coming months. After this date, any application connecting to Exchange Online will be required to leverage modern authentication (OAuth 2.0). Microsoft will continue to disable basic authentication on any newly created Office 365 tenants.
For devices and applications that integrate with Exchange Web Services, such as voicemail, ticketing systems, or line of business applications, these will also be required to support modern authentication.
For PowerShell, I recommend using the Microsoft Exchange Online PowerShell Module. This module supports both modern-authentication and is a requirement if your admin account has multi-factor authentication enabled (which I hope it does!). I recommend checking out this article for more information on how to use this module. Also, you may want to look into the Azure Cloud Shell. Check out the tutorial; Using Exchange Cmdlets in Azure Cloud Shell.
For POP and IMAP, Microsoft recently added OAuth support. However, this still requires your POP or IMAP application to support OAuth. Microsoft will also be releasing a tool to help you identify active POP and IMAP users in Office 365 and what authentication mechanism they are currently using.
The most significant impact of this announcement will be to ActiveSync. ActiveSync is used by countless native mail apps to access their Office 365 mail. I highly recommend migrating your user base to Outlook mobile (for iOS and Android). Outlook Mobile supports both modern authentication and multi-factor authentication. It is worth noting that some native mail apps, such as those included in iOS 11, have added support for modern authentication. However, pushing users to Outlook Mobile, versus upgrading their phones, is the path of least resistance. Not to mention your helpdesk or IT department will only need to support one universal mail client.
To track which devices and applications are signing in with basic authentication, you can use the Azure AD Sign-ins dashboard. Microsoft covers this process in this article.
If you are interested in how to block basic authentication on-prem with Exchange 2019, check out this article, Disabling Legacy Authentication in Exchange Server 2019.
More in Awesome
One of the challenges of a large Exchange Online organization is that PowerShell commands can take a very long time to run. To combat this problem, the Exchange Team released the Exchange Online PowerShell V2 module, which ships with all new Exchange cmdlets. Microsoft has determined that in certain instances, these new cmdlets are up to eight times faster than their former counterparts. This module is now considered generally available.
Further Reading
Here are some articles I thought you might like.
- Recover deleted email in a user’s mailbox
- Hybrid Configuration Wizard fails: WinRM client cannot process the request
- Use Log Parser Studio in your Exchange & Office 365 migration planning
- Blocking OneDrive may save attachments to the default SharePoint document library
- RPC/HTTP & Block Legacy Auth may prevent Outlook reconfiguration after migrating to Exchange Online

So what do you think is coming next? What would you like to see? Drop a comment below or join the conversation on Twitter @SuperTekBoy.


Leave a Reply