Plus Addressing in Exchange Online
During Ignite 2020, Microsoft announced that plus addressing was coming to Exchange Online. Plus addressing allows users to create their own unique email addresses by leveraging a plus sign in their email address—for example, john.smith+newsletter@contoso.com. Anything after the plus sign is completely at the discretion of the user.
This becomes particularly useful when you want to target newsletters to a unique email address, especially when configuring inbox rules. It is also useful to determine who might have sold or leaked your email address.
To leverage this feature, an administrator must enable it globally (by default, it is disabled). To do this, log onto Exchange Online PowerShell. First, let’s verify if plus addressing is disabled. We do this with the following command.
C:\> Get-OrganizationConfig | FL AllowPlusAddressInRecipients AllowPlusAddressInRecipients : False
From our output, we can see that plus addressing is disabled in our tenant. To enable, run the following command.
C:\> Set-OrganizationConfig -AllowPlusAddressInRecipients $true
To confirm the setting has taken effect, rerun Get-OrganizationConfig.
Users can then start leveraging plus addresses. Emails addressed to a plus address will appear in the user’s inbox without any further user intervention. From there, the user can build inbox rules for the plus addresses if they desire.
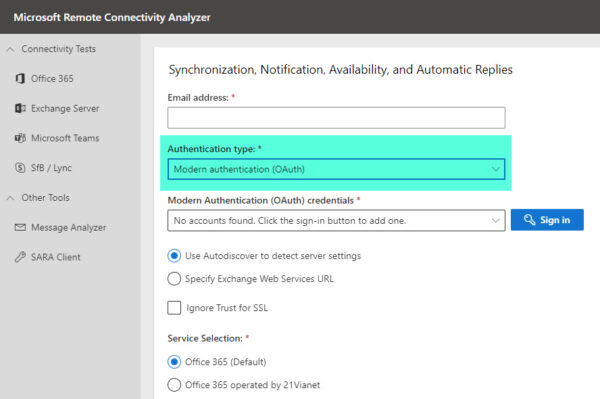
Remote Connectivity Analyzer Supports Modern Auth
The remote connectivity analyzer is a fantastic tool for troubleshooting Exchange issues. It is especially useful when troubleshooting Outlook connectivity, free/busy, ActiveSync, and more.
One limitation of the tool has been its inability to test accounts with modern authentication. This is particularly problematic where legacy authentication is blocked. The workaround was to temporarily allow the account access via legacy auth. Thankfully, Microsoft has added modern auth to the remote connectivity analyzer.
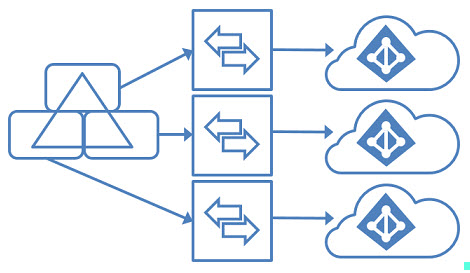
Hybrid Wizard now supports multiple Exchange Online tenants
In September, Microsoft announced that they now support a single on-premises Exchange organization to multiple Exchange Online tenants (currently up to 5 tenants).
This functionality will require the latest version of the hybrid configuration wizard and Exchange 2016 CU18+ or Exchange 2019 CU7+.
Users cannot be synchronized to more than one Azure tenant. This means Azure AD Connect must be configured for domain or OU filtering, where each OU (or domain) is targeted to a specific Azure Active Directory instance. There must be no overlap where users are synchronized to two or more Azure AD instances.
Also, because domains can only be validated against a single Office 365 tenant, each filter scope will need its own unique SMTP domain. Migrating a user to an Office 365 tenant where the domain does not exist, will remove that SMTP address from that user. However, this requirement could eventually change as SMTP domain sharing was announced as a public preview program back in September.
Note: At present, Hybrid Modern Authentication is not supported when you connect more than one tenant. Microsoft is working to remediate this issue.
Outlook REST APIs deprecated
Microsoft will be deprecating the Outlook REST APIs in favor of the Microsoft Graph APIs. The Outlook REST APIs will be fully decommissioned on November 30th, 2022. Any third-party developer who uses the Outlook REST API as an entry point into Office 365 will need to reconfigure their application or service to use the Microsoft Graph API instead. Integrations using REST will be denied after November 30th, 2022.
For customers of third-party applications, check with your vendor to see if you need to perform an upgrade or take any action to make sure your application will continue to work with Office 365 after November 30th, 2022.
Root certificate changes for the hybrid agent
Microsoft will be leveraging a new root certificate authority in Azure. This new certificate authority will result in changes to the root certificates used by Azure. Organizations that restrict root certificate updates or access to certificate revocation lists and use the hybrid agent could be impacted by the Azure TLS certificate change.
An organization with this configuration will need to permanently update its rules or temporarily allow access to the following certificate revocation lists. If this access cannot be granted, then organizations will need to update their root certificates manually.
- http://crl3.digicert.com
- http://crl4.digicert.com
- http://ocsp.digicert.com
- http://www.d-trust.net
- http://root-c3-ca2-2009.ocsp.d-trust.net
- http://crl.microsoft.com
- http://oneocsp.microsoft.com
- http://ocsp.msocsp.com
Legacy Authentication deadline extended till 2021
Microsoft previously announced that it was blocking legacy authentication in Exchange Online on October 13th, 2020. Due to the global pandemic, this date was postponed to the second half of 2021. Microsoft will propose an exact deadline in the coming months. After this date, any application connecting to Exchange Online will be required to leverage modern authentication (OAuth 2.0). Microsoft will continue to disable legacy authentication on any newly created Office 365 tenants.
For devices and applications that integrate with Exchange Web Services, such as voicemail, ticketing systems, or line of business applications, these will also be required to support modern authentication.
For PowerShell, I recommend using the Microsoft Exchange Online PowerShell Module. This module supports both modern-authentication and is a requirement if your admin account has multi-factor authentication enabled (which I hope it does!). I recommend checking out this article for more information on how to use this module. Also, you may want to look into the Azure Cloud Shell. Check out the tutorial; Using Exchange Cmdlets in Azure Cloud Shell.
For POP and IMAP, Microsoft recently added OAuth support. However, this still requires your POP or IMAP application to support OAuth. Microsoft will also be releasing a tool to help you identify active POP and IMAP users in Office 365 and what authentication mechanism they are currently using.
The most significant impact of this announcement will be on ActiveSync. Countless native mail apps use ActiveSync to access their Office 365 mail. I highly recommend migrating your user base to Outlook mobile (for iOS and Android). Outlook Mobile supports both modern authentication and multi-factor authentication. It is worth noting that some native mail apps, such as those included in iOS 11, have added modern authentication support. However, pushing users to Outlook Mobile versus upgrading their phones is the path of least resistance. Not to mention your helpdesk or IT department will only need to support one universal mail client.
To track which devices and applications are signing in with legacy authentication, you can use the Azure AD Sign-ins dashboard. Microsoft covers this process in this article.
Once you have eliminated legitimate legacy auth clients, you can then move to block legacy auth altogether. Microsoft allows administrators to disable legacy auth by the client type. These settings are found in the main Microsoft 365 Admin Center by navigating to Settings > Org Settings > Modern Authentication.
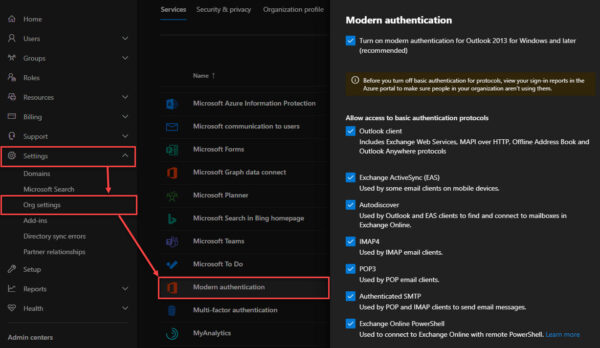
If you need granularity, especially if you need to make exceptions for legacy auth, I recommend implementing conditional access policies instead.
Multi-Geo expands to Germany and Norway
Microsoft has announced that it will be expanding multi-geo coverage to Germany and Norway. Multi-Geo is a feature that allows organizations to place their user’s data in a geography that is different than where the main tenant is located. For example, a company headquartered in the United States with satellite offices in the United Kingdom and Germany could designate their home geo (for the bulk of their users) as the United States and place their United Kingdom and German users into data centers in those regions. This is to satisfy data residency laws.
Office 365 Government certified as FedRAMP High
Microsoft announced in October that its Office 365 GCC offering (for government agencies) has been certified as FedRAMP High. FedRAMP is an assessment performed by the U.S. Federal Government to ensure the proper security of cloud providers.
Office 365 tenants designated as GCC and GCC High are designed specifically with the security and compliance requirements of the U.S. federal, state, local, and tribal governments (including government contractors).
Need a refresher from Ignite 2020?
With Ignite 2021 only a few months away (March 2–4, 2021), it might be time to brush up on some of the topics covered at the last Ignite. If you need a refresher on all the Exchange features announced at Ignite, I highly recommend checking out the article 15 Ignite sessions every Exchange admin should see (2020 edition). In this article, there are extensive notes on what each session contained. Also, those notes include timers if you need to jump to a specific topic.
Further Reading
Here are some articles I thought you might like.
- RunAs Radio #745 – Exchange Server vNext announced
- 15 Ignite sessions every Exchange admin should see (2020 Edition)
- Exchange Server Cumulative Updates (December 2020)
- Use Log Parser Studio in your Exchange & Office 365 migration planning
- RPC/HTTP & Block Legacy Auth may prevent Outlook reconfiguration after migrating to Exchange Online

So what do you think is coming next? What would you like to see? Drop a comment below or join the conversation on Twitter @SuperTekBoy.

Leave a Reply